
A team of researchers from China’s Pangu Lab recently published a 56-page report detailing a piece of Linux malware allegedly used against many targets by the threat actor known as the Equation Group, which has been linked to the U.S. National Security Agency (NSA).
Pangu Lab is a research project of Pangu Team, which is best known for its iPhone jailbreaks. An iOS exploit earned them $300,000 last year at a major Chinese hacking contest.
Discovery of backdoor in Chinese government system
In 2013, during an in-depth forensic investigation of a host in a key Chinese government department, researchers from the Pangu Lab extracted a set of advanced backdoors on the Linux platform, which used advanced covert channel behavior based on TCP SYN packets, code obfuscation, system hiding, and self-destruction design.
Among the many clues of attacks against China, the earliest one can be traced back to 2002.
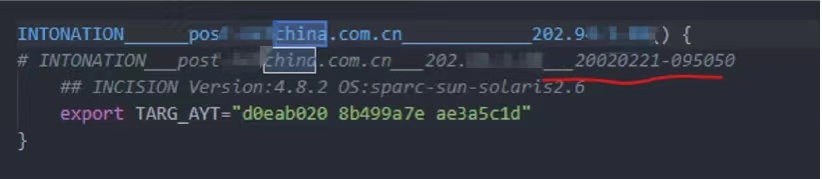
It is further found that this backdoor needs the check code bound to the host to run normally. Then the researchers cracked the check code and successfully ran the backdoor. Judging from some behavioral functions, this is a top-tier APT backdoor, but further investigation requires the attacker’s asymmetric encrypted private key to activate the remote control function. The team named the corresponding malicious code “Bvp47” at the time.
The team reproduced the use of the Bvp47 backdoor in its own environment and roughly clarified its usage scenarios and basic communication mechanisms. As an important backdoor platform for long-term control of victims after a successful invasion, Bvp47 generally lives in the Linux operating system in the demilitarized zone that communicates with the Internet. It mainly assumes the core control bridge communication role in the overall attack, as shown below.
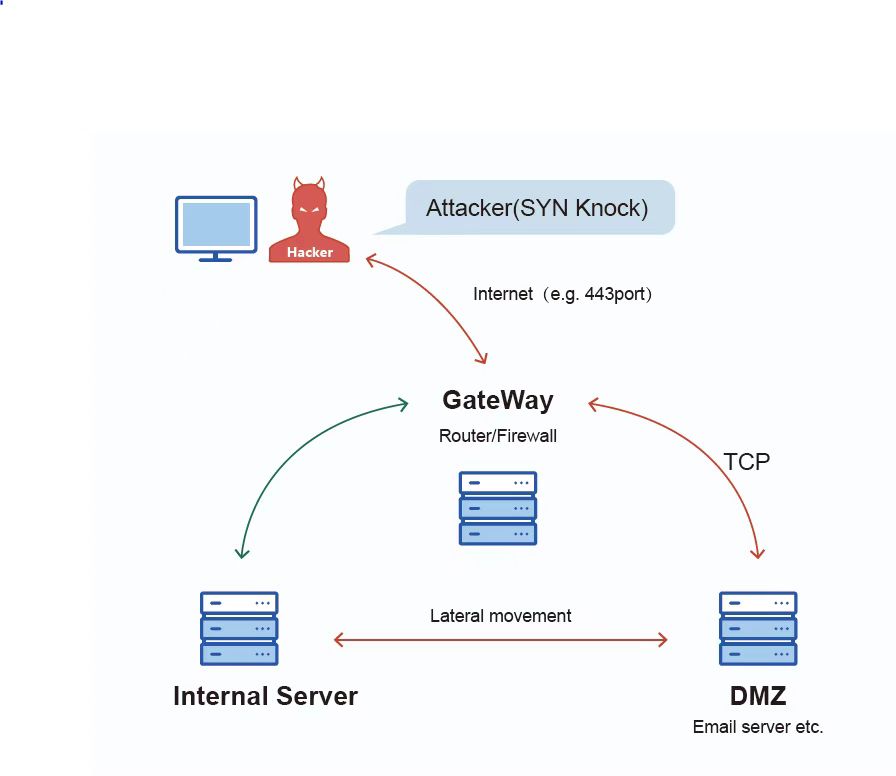
Bvp47 builds its covert communication system from cryptography, network, and Linux OS. Such a covert communication system is cutting edge and can be seen as an advanced version of “SYNKnock” (the old version of Cisco devices only conducts simple verification).
In 2016 and 2017, “The Shadow Brokers” published two batches of hacking files claimed to be used by “The Equation Group”. In these hacking files, researchers from Pangu Lab found the private key that can be used to remotely trigger the backdoor Bvp47. Therefore, It can be concluded that Bvp47 is a hacker tool belonging to ” The Equation Group”.
Through further research, the researchers found that the multiple procedures and attack operation manuals disclosed by “The Shadow Broker” are completely consistent with the only identifier used in the NSA network attack platform operation manual exposed by CIA analyst Snowden in the “Prism” incident in 2013.
Connection with Snowden Incident
In December 2013, the German media “Der Spiegel” published an NSA ANT catalog with 50 pictures. This is a series of top-secret materials compiled by the NSA in 2008-2009, including the use of a series of advanced hacking tools. The source of information may come from Edward Snowden or another unknown intelligence provider.
According to one file named “SecondDate” in the NSA ANT catalog, the team found that there are more than 90 related programs that span multiple platforms and architectures, such as Windows, Linux, Solaris, etc. Moreover, the relationship between the program is also clarified in the “EquationGroup-master\Linux\etc” directory. Therefore, there are enough reasons to believe that the files leaked by Shadow Brokers in 2016 and 2017 belonged to the NSA Equation group’s hacking tools, that is, Bvp47 is the top-tier backdoor of NSA.
Global victims of NSA attack
Besides, the files of “The Shadow Brokers” revealed that the scope of victims exceeded 287 targets in 45 countries, including Russia, Japan, Spain, Germany, Italy, etc. The attack lasted for over 10 years.

A list of potential backdoor victims is provided in the eqgrp-auction-file.tar.xz.gpg file\Linux\bin\varkeys\pitchimpair\ directory. The victims are all over the world, including some key units of China.
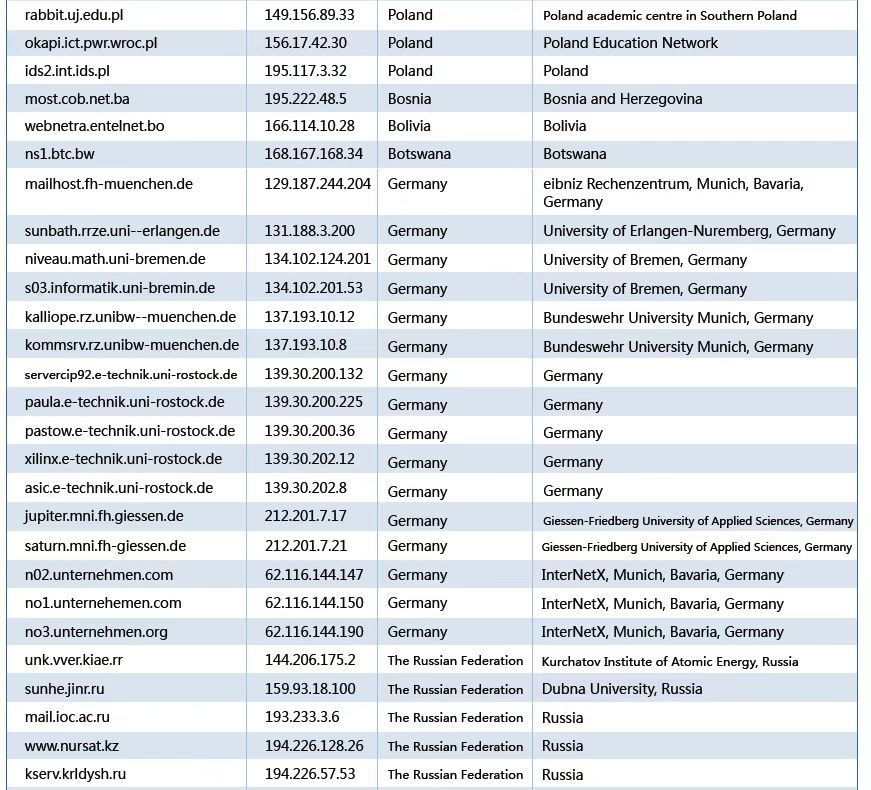
Technical details are revealed
The implementation of Bvp47 includes complex code, segment encryption and decryption, Linux multi-version platform adaptation, rich rootkit anti-tracking techniques, and most importantly, it integrates an advanced BPF engine used in advanced covert channels, as well as a cumbersome communication encryption and decryption process.
There are several key points in the program initialization as follows:
- Linux user mode and kernel mode
- Initialize the Bvp engine
- A series of environmental tests
- A series of payload block decryption
- Tamper with kernel devmem restrictions to allow processes in user mode to directly read and write kernel space
- Load non-standard lkm module files
- Hook system function in order to hide its own process, file, network, and self-deleting detection in the covered channel communication
The entire file of Bvp47 adopts the commonly used backdoor packaging method, that is, the backdoor function modules are compressed and assembled and then placed at the end of the file, and the whole file exists in the form of additional data. The additional data is loaded through the loader function module built into the program, which mainly completes the following steps: read, check, unzip, decryption, and load.
The Equation Group is the world’s leading cyber-attack group and is generally believed to be affiliated with the National Security Agency of the United States. Judging from the attack tools related to the organization, including Bvp47, Equation group is indeed a first-class hacking group.

The tool is well-designed, powerful, and widely adapted. Its network attack capability equipped by 0day vulnerabilities was unstoppable, and its data acquisition under covert control was with little effort. The Equation Group is in a dominant position in national-level cyberspace confrontation.
As an advanced attack tool, Bvp47 has allowed the world to see its complexity, pertinence and forward-looking. What is shocking is that after analysis, it has been realized that it may have existed for more than ten years.
Even as a cyber security team that insists on high-precision technology-driven, Pangu team could only protect users in future cyber confrontations by actively exploring the cutting-edge technology of information security attack and defense, keeping track of important incidents, and coordinating with cybersecurity professionals globally. And it took so many years to identify and analyze all the details, meanwhile the NSA already took essential information it needs from many important units of different countries.
(Source: Pangu Lab, Sohu, wodesign)



